
- Introduction to Vigenere Cipher
- Historical Background
- How the Cipher Works
- Vigenere Table (Tabula Recta)
- Encryption Process
- Decryption Process
- Strengths and Weaknesses
- Vigenere vs Caesar Cipher
- Cryptanalysis Techniques
- Real-World Examples
- Summary and Applications
Introduction to Vigenere Cipher
The Vigenere Cipher is a classical method of encrypting alphabetic text using a series of Caesar ciphers based on the letters of a keyword. Named after Blaise de Vigenere, a French cryptographer, this cipher improves upon simpler substitution ciphers by introducing polyalphabetic substitution. By using a key to control the shifting of letters, the Vigenere Cipher is more secure than monoalphabetic ciphers and was once considered unbreakable. The Vigenere Cipher belongs to the family of polyalphabetic substitution ciphers. Unlike monoalphabetic ciphers, which use a single alphabet for the entire message, Vigenère changes the substitution for each letter depending on a repeating keyword a technique that makes the cipher significantly harder to crack using traditional frequency analysis. Understanding such encryption strategies is a vital part of Cyber Security Training, which equips professionals with the knowledge to analyze, protect, and decode sensitive data. The core idea is to shift each letter of the plaintext by an amount determined by the corresponding letter in the key. The cipher’s design was considered a significant improvement over earlier substitution methods when it was first introduced. It was used by military and diplomatic communications for centuries, as it provided better security through its polyalphabetic structure. However, its strength has limits. Skilled cryptanalysts can sometimes uncover the pattern using more advanced techniques, especially if the key is short or the message is long. Still, the Vigenere cipher remains an important step in the history of cryptography because it demonstrates how combining simple ideas like shifting letters based on a repeating keyword can dramatically increase security.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Historical Background
Although named after Blaise de Vigenere, the cipher was first described by Giovan Battista Bellaso in 1553. Vigenere later developed a more secure version of Bellaso’s method, which led to the association of the cipher with his name. For centuries, it was considered a strong method of encryption and earned the nickname “le chiffre indechiffrable” (the indecipherable cipher). It remained unbroken until the 19th century when Charles Babbage and Friedrich Kasiski developed techniques to crack it. For many centuries, the Vigenère cipher was considered virtually unbreakable. To understand how even historically trusted algorithms can become exploitable over time, explore Cybersecurity Vulnerabilities a foundational guide that explains how weaknesses in cryptographic systems, software, and configurations are identified, exploited, and mitigated in modern security frameworks. It earned the nickname “le chiffre indechiffrable,” which means “the indecipherable cipher” in French. This nickname highlights how powerful and difficult to crack this code was viewed at the time. Governments and spies relied on it to protect sensitive information, confident that it could withstand any attack from opponents. During this era, the cipher was seen as a reliable shield, safeguarding secrets from prying eyes.
How the Cipher Works
The Vigenere Cipher works by combining a plaintext message with a repeating keyword. Each letter of the keyword corresponds to a shift in the alphabet. For example, if the keyword is “KeY” and the message is “HeLLO”, Understanding the Vigenère Cipher helps build foundational knowledge in cryptography, which is essential when addressing Web security threats and solutions especially for designing secure communication channels and protecting sensitive data. The encryption works as follows:
- H shifted by K (10 positions)
- e shifted by e (4 positions)
- L shifted by Y (24 positions)
- L shifted by K (10 positions)
- O shifted by e (4 positions)
- Key: D
- Plaintext: B
- Ciphertext: e (Row D, Column B)
- Resistant to frequency analysis: Makes standard decryption methods less effective.
- Polyalphabetic substitution: Makes patterns less visible in ciphertext.
- Easy to implement manually: Especially with tools like the Tabula Recta.
- Stronger than Caesar or monoalphabetic ciphers: Offers higher complexity and variability.
- Repeating keys can be detected: Leads to vulnerability if the pattern is discovered.
- Vulnerable to Kasiski examination and Friedman test: These statistical methods can expose the key length.
- Short keys reduce effectiveness: Easier to break with modern techniques.
- Requires key sharing: Both sender and receiver must securely exchange and protect the key.
- Kasiski examination: Identifies repeated sequences in ciphertext to estimate key length.
- Friedman Test: Uses statistical measures like the index of coincidence to approximate key length.
- Known Plaintext Attack: If some part of the plaintext is known, the key can be deduced.
- Frequency Analysis by Subtext: Once key length is known, ciphertext is divided into subtexts encrypted with the same Caesar cipher and analyzed individually.
- Historical Use: Used by diplomats and military officers in the 16th–19th centuries.
- Educational Use: Taught in cryptography classes to illustrate polyalphabetic encryption.
- Spy Communication: Occasionally used by amateur spies or in puzzle games.
- CTF Challenges: Commonly featured in Capture The Flag cybersecurity competitions.
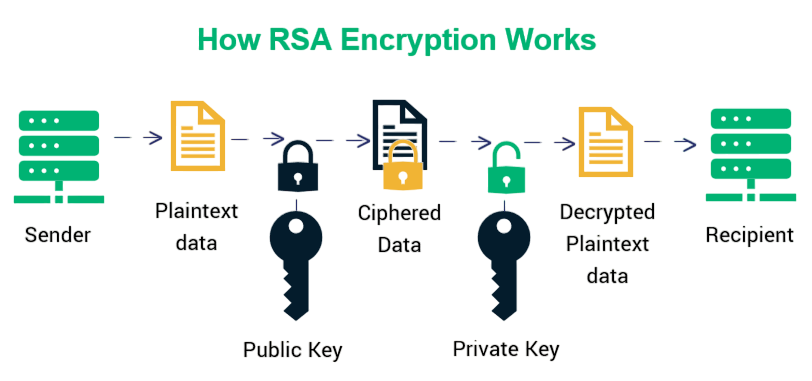
The result is a ciphertext that appears random and resists analysis. The key must be known for decryption.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Vigenere Table (Tabula Recta)
The Vigenere Table, or Tabula Recta, is a 26×26 matrix of the alphabet. each row represents a Caesar cipher shift for a corresponding letter. The top row starts with ‘A’, the next row starts with ‘B’, and so on until ‘Z’. To encrypt a letter, find the intersection of the row corresponding to the key letter and the column of the plaintext letter. For those interested in broader cyber defense strategies, it’s crucial to learn what is a ddos attack, as understanding different threats helps reinforce protection at every level of communication.
For example:
The Tabula Recta simplifies both encryption and decryption by providing a visual tool for letter substitution.
Encryption Process
To encrypt a message with the Vigenere Cipher, start by choosing a keyword, like “LeMON.” Next, repeat this keyword so it matches the length of the plaintext message. Once you align them, pair each letter of the plaintext with the corresponding letter from the keyword. To create the ciphertext, shift each plaintext letter based on the position of the key letter in the alphabet a foundational technique used in classic encryption methods. Learning this approach is an important component of Cyber Security Training, where understanding cipher mechanics helps build stronger data protection strategies. You can do this using the Tabula Recta or by adding the key letter’s position. For instance, if the plaintext is “ATTACKATDAWN” and the repeated key is “LeMONLeMONLe,” the ciphertext will be “LXFOPVeFRNHR.” This method creates a cipher that is more complex and less predictable than a traditional monoalphabetic substitution, improving the security of the encrypted message.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Decryption Process
Decryption is the back process of encryption. It involves several ways to recover the original communication. First, repeat the keyword until it matches the length of the ciphertext. Also, align each letter of the ciphertext with the matching letter of the key. Using the Tabula Recta, find the row that matches the crucial letter an essential step in classical ciphers like Vigenere. This method forms the backbone of many Encryption and Decryption Concepts, helping illustrate how shifting patterns and key-based substitutions secure sensitive information. In this row, detect the ciphertext letter. From there, identify the column heading to reveal the plaintext letter. For illustration, with the ciphertext” LXFOPVeFRNHR” and the crucial” LeMONLeMONLe,” the decryption process gives the plaintext” ATTACKATDAWN.” This system ensures a correct recovery of the original communication as long as the right key is used.
Strengths and Weaknesses
Strengths:
Weaknesses:
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Vigenere vs Caesar Cipher
The Caesar Cipher is a special case of the Vigenere Cipher with a single, constant shift. The key difference is: The Caesar Cipher is a type of monoalphabetic substitution cipher that uses a single fixed shift to encode messages. In contrast, the Vigenere Cipher is a more complex polyalphabetic cipher that changes its shifts based on a specific keyword. This difference between the two ciphers shows the various ways to encrypt information, highlighting the evolving complexity of digital protection. Such innovations are key in shaping the future of cyber physical system, where secure communication and integrated technologies must work hand-in-hand to protect both digital and physical assets. The Caesar Cipher relies on a simple method, while the Vigenere Cipher adds complexity by using multiple shifting patterns based on the selected keyword. While Caesar is easy to break with frequency analysis, Vigenere is more secure due to its dynamic nature. However, both can be compromised with modern cryptanalysis if used improperly.
Cryptanalysis Techniques
Several methods have been developed to break the Vigenère Cipher:
These methods demonstrate that while Vigenère is strong against simple attacks, it is not unbreakable.
Real-World examples
Though obsolete for secure communication today, the Vigenère Cipher has been used historically and educationally:
These examples show its relevance in historical context and as a foundational concept in learning cryptography.
Summary and Applications
The Vigenere Cipher is a classical encryption technique that marked a significant advancement in cryptography. By introducing polyalphabetic substitution, it addressed many weaknesses of simpler ciphers. Despite being eventually cracked, it remains an important educational tool. Its applications include: Teaching cryptographic principles requires a strong grasp of historical research. This research offers valuable context and insight into how encryption techniques have evolved over time, making it a valuable resource for professionals undergoing Cyber Security Training, where understanding the history of cryptographic methods strengthens modern data defense strategies. Educators can use this knowledge when designing puzzles and escape rooms. In these activities, participants face cryptographic challenges that encourage critical thinking and problem-solving. By incorporating these elements, educators can create engaging learning experiences. These experiences not only teach participants the basics of cryptography; they also emphasize its importance in history. Understanding the Vigenere Cipher provides insight into the evolution of encryption methods and highlights the importance of key management and cryptanalysis techniques in secure communication.




